- NSX Manager – Replace Certificates
 After you install NSX, the manager nodes and cluster have self-signed certificates. Replace the self-signed certificates with a CA-signed certificate and use a single common CA-signed certificate with a SAN (Subject Alternative Name) that matches all the nodes and the VIP for the cluster. Prerequisites Procedure We will show how we can do this without any… Read more: NSX Manager – Replace Certificates
After you install NSX, the manager nodes and cluster have self-signed certificates. Replace the self-signed certificates with a CA-signed certificate and use a single common CA-signed certificate with a SAN (Subject Alternative Name) that matches all the nodes and the VIP for the cluster. Prerequisites Procedure We will show how we can do this without any… Read more: NSX Manager – Replace Certificates - Remove NSX Password Expiration
 VMware NSX has a preconfigured password expiration policy of 90 days. When the password expiration day is near, a notification is displayed in the Web interface. There are 3 preconfigured local users: admin, audit, and root. All passwords have to be changed after 90 days https://docs.vmware.com/en/VMware-NSX/4.2/installation/GUID-89E9BD91-6FD4-481A-A76F-7A20DB5B916C.html Please keep in mind that not only the password… Read more: Remove NSX Password Expiration
VMware NSX has a preconfigured password expiration policy of 90 days. When the password expiration day is near, a notification is displayed in the Web interface. There are 3 preconfigured local users: admin, audit, and root. All passwords have to be changed after 90 days https://docs.vmware.com/en/VMware-NSX/4.2/installation/GUID-89E9BD91-6FD4-481A-A76F-7A20DB5B916C.html Please keep in mind that not only the password… Read more: Remove NSX Password Expiration - Troubleshoot Network Using Packet Capture
 Packet Capture Edge Traffic on ESXi Find NIC Where Traffic Flows Method A Login to ESXi shell and use command ESXTOP → N to find NIC for Edge node. Method B Login to ESXi shell and use commands: “Port ID:” and “Team Uplink:” will give the respective switchport and uplink. Once the Switchport and vmnic is figured,… Read more: Troubleshoot Network Using Packet Capture
Packet Capture Edge Traffic on ESXi Find NIC Where Traffic Flows Method A Login to ESXi shell and use command ESXTOP → N to find NIC for Edge node. Method B Login to ESXi shell and use commands: “Port ID:” and “Team Uplink:” will give the respective switchport and uplink. Once the Switchport and vmnic is figured,… Read more: Troubleshoot Network Using Packet Capture - Troubleshooting NSX “Transport node with IP already exists”
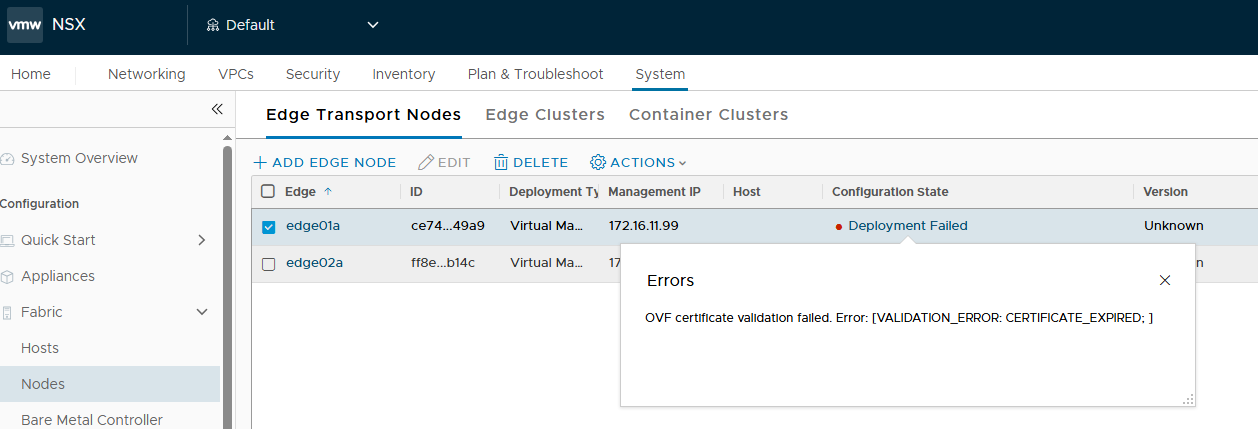
 We had a project where we replace the old hosts with the new ones and use the same IP addresses. Everything was fine until we put the new hosts back into the cluster and NSX preparations task kick in. Then NSX manager gives as validation error. It states: “26210: Node duo-11 with 10.10.10.1 already exists”.… Read more: Troubleshooting NSX “Transport node with IP already exists”
We had a project where we replace the old hosts with the new ones and use the same IP addresses. Everything was fine until we put the new hosts back into the cluster and NSX preparations task kick in. Then NSX manager gives as validation error. It states: “26210: Node duo-11 with 10.10.10.1 already exists”.… Read more: Troubleshooting NSX “Transport node with IP already exists” - Processing Order of NAT Rules.
 In short, by assigning NAT rules to a policy, you can control the order in which the rules are processed. The first matching rule in the policy is applied, and subsequent rules are skipped. To validate the order of NAT rules within NAT policies and ensure they are evaluated correctly you can follow these steps:
In short, by assigning NAT rules to a policy, you can control the order in which the rules are processed. The first matching rule in the policy is applied, and subsequent rules are skipped. To validate the order of NAT rules within NAT policies and ensure they are evaluated correctly you can follow these steps:
NSX
Hello,
I’m Aigars

Welcome to Virtualisation Alley, my cozy corner of the internet dedicated to VMware. Here, I invite you to join me on a journey into virtual world. Let’s go.
Let’s connect