After you install NSX, the manager nodes and cluster have self-signed certificates. Replace the self-signed certificates with a CA-signed certificate and use a single common CA-signed certificate with a SAN (Subject Alternative Name) that matches all the nodes and the VIP for the cluster.
Prerequisites
- Import certificate to NSX Manager.
- The server certificate must contain the Basic Constraints extension
basicConstraints = cA:FALSE.
Procedure
We will show how we can do this without any special utilities using only the CURL command. The certificate chain must be in the industry standard order of “certificate – intermediate – root.” Make sure that when this certificate was imported, the option Service Certificate was set to No.
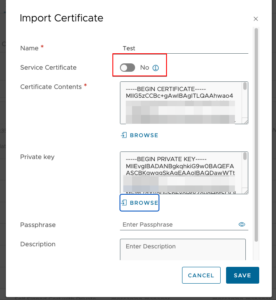
Before we can replace certificate, we need 4 id’s:
- Certificate ID
- Node ID NSX-Manager1
- Node ID NSX-Manager2
- Node ID NSX-Manager3
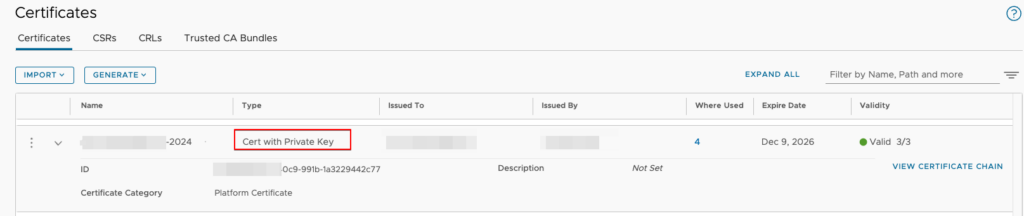
Certificate ID
We get the certificate ID from the certificate details.
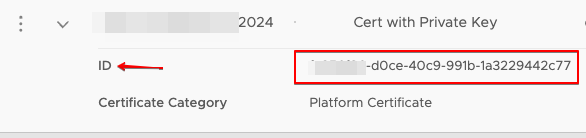
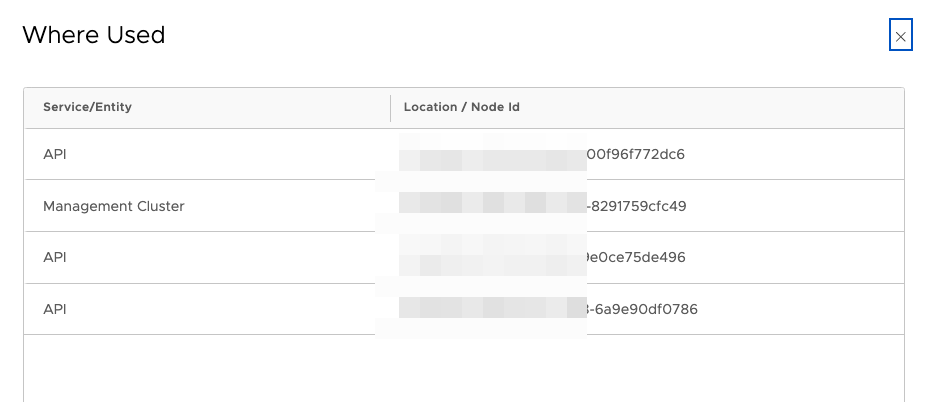
Node ID
We get the node ID from the NSX Manager UI under System > Appliances > NSX Manager. Click on blue link “View Details” then we get more information about the manager nodes.
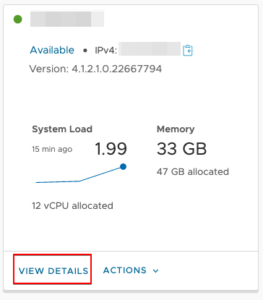
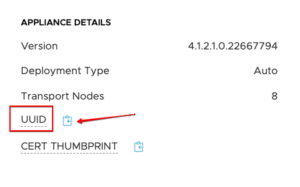
With this collected information we can now verify and replace the NSX Manager certificate.
Validate
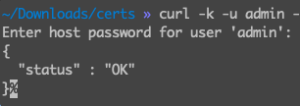
Before replacing the certificates, the new certificate should be validated. Replace NSX manager FQDN and Cert ID! API call can be executed on any terminal which can connect to NSX.
curl -k -u admin -X GET "https://[NSX FQDN]/api/v1/trust-management/certificates/[Cert ID]?action=validate"In case of success we will get return code – OK.
Changing Manager Certificates
Replace manager Node ID, FQDN and Cert ID. If you have 3 managers then you should repeat this command 3x times.
curl -k -u admin -X POST 'https://[NSX FQDN]/api/v1/trust-management/certificates/[Cert ID]?action=apply_certificate&service_type=API&node_id=[Node ID]'There’ll be no return value in case of success.
Changing VIP Certificate
Replace manager FQDN and Cert ID.
curl -k -u admin -X POST 'https://[NSX FQDN]/api/v1/trust-management/certificates/[Cert ID]?action=apply_certificate&service_type=MGMT_CLUSTER'When it’s done you can check certificate in NSX UI.